How Gamification Can Boost Retention on Any App Part 3: Techniques to Keep Users Coming Back & Increase Retention
The Mystic Media Blog is currently endeavoring on a 3 part series on how gamification mechanics can boost retention on any app—not just gaming apps but utility apps, business apps and more. In this third entry, we explore additional techniques to keep users coming back and increase retention.
Your users have downloaded your app and are acclimated with its features. You’ve perfected your core loop to ensure users can complete meaningful actions in the app on a daily basis. Now the question becomes—how can you retain ongoing usage? The average cost to acquire a mobile app user is $4, yet retention rates can quickly drop from there. Statistics show that a 5% increase in retention can boost profitability by up to 75%.
There are a variety of techniques employed by mobile games that app developers can use in their non-gaming apps to keep users engaged long after the application ends.
INVEST IN THE FUTURE
An optimized application development process requires thinking about how your product can evolve beyond the initial release. Often this is due to schedule and budgetary constraints. It is natural in any creative endeavor to have more ideas than time and money to complete them. However, thinking long-term can be an advantage. New features entice users to continue using the application after download and to allow push notifications for fear of missing out on updates.
Mobile games often have to confront this since the amount of content they offer is finite—a certain amount of levels, achievements, and unlockables which can be completed. Games can offer additional modes and levels to entice users to come back. Similarly, non-gaming apps can offer new content—such as informative blogs, new features, and new product lines.
During the development process, plan out multiple phases and deliver new features and content updates on a regular basis. If you have a blog, host it on your application and keep users coming back for content updates.
IMPLEMENT SOCIAL FEATURES
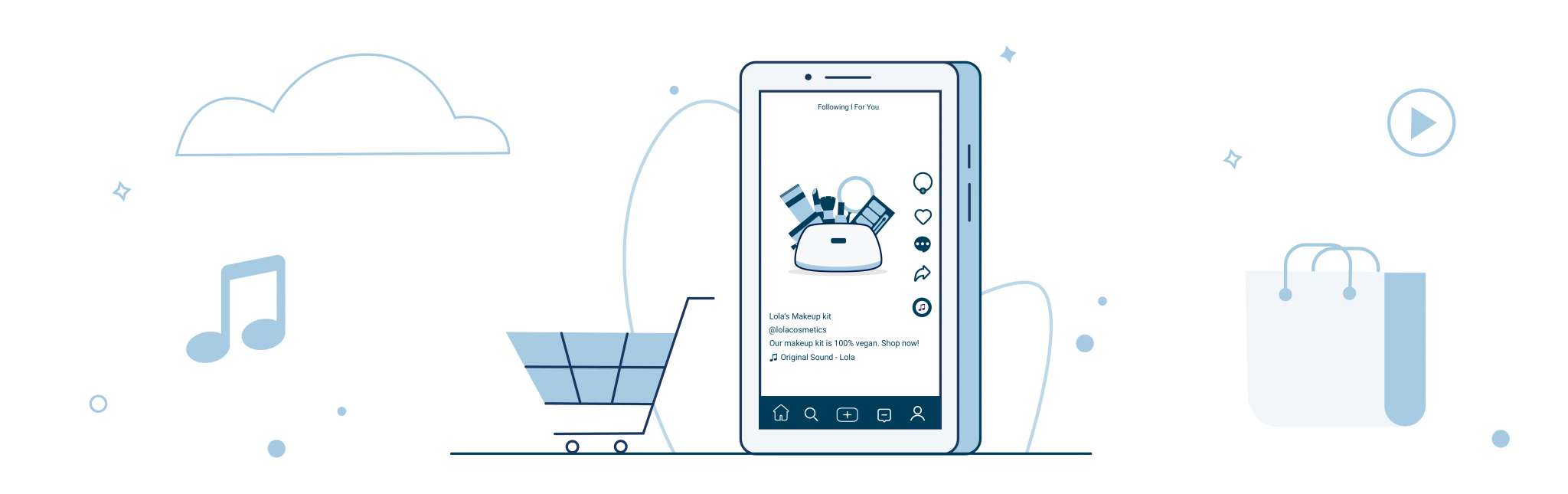
Game developers know that “Socializers”, or users who thrive on social interaction, constitute one of the most important Bartle Types. Social features are crucial not only to retaining interest and daily usage of an application, but as a marketing technique to encourage users to engage with one another and spread the word. Once your userbase is established, implementing social features will increase engagement.
Consider implementing the following social features in phase 2 of your application:
- Customizable user profiles: Enabling usernames, profile pictures, bios and other user customization features help users feel more connected to the app vis a vis their profile.
- Rewarded social sharing: Encourage users to spread the love by rewarding them with discounts and reward points when they share to social media.
- Likes and comments on products: Implementing comments and likes not only gives users another avenue for engagement, it creates a platform for automated push notifications that will likely result in more daily opens.
- Follow and friend other users: Allowing users to connect can result in meaningful social relationships which will increase their connection with your application.
- Rewarded actions: Encourage users to complete an action for the first time by offering them some kind of reward.
PUSH NOTIFICATIONS STRATEGY
Push notifications are integral to every app developers’ retention strategy. They are the most effective vessel for delivering timely reminders and relevant notifications about new features on applications. Users can disallow push notifications at any time, so developers need to pick their spots or risk losing one of their most prized tools.
When developing your push notification strategy, consider the following:
- Timing: Rather than sending push notifications all at once, target users based on their time zone. Make sure the timing of your notifications makes sense based on the message.
- Personalization: Optimize UI by tracking app usage data and leveraging it for personalized push notifications. Personalize push notifications based on a user’s behavior such as their purchase history to help build app loyalty and keep notifications relevant.
- Prudence: If you bombard users with irrelevant notifications, the decision to unsubscribe to push notifications becomes easy. Exercise restraint when sending push notifications and only send valuable information and reminders.
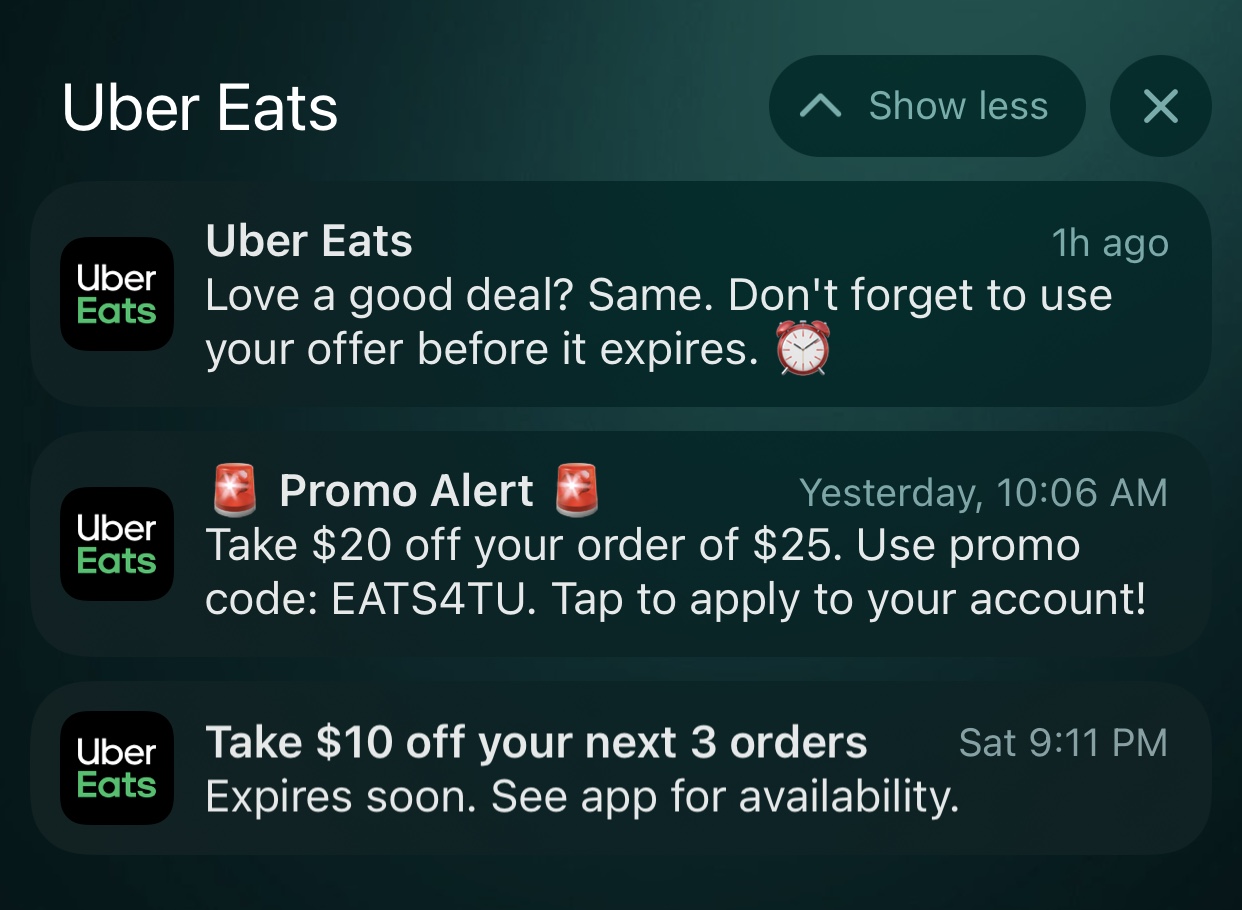
Users are always looking for value and discount—which is why delivery and transportation applications often use push notifications to send discount codes. Shopping apps can also send push notifications which notify users when they have items left in their cart—a timely prompt to finish the purchase can directly lead to revenue.
KEEP INNOVATING
The app development process does not have to end with an apps initial release into app stores. Rolling out new features to maintain engagement with your audience and bolster your application will result in improved retention.